Indicators of compromise (IoCs)
Indicators of compromise (IoCs) are clues or evidence that suggest a system or network has been breached or is under attack. This forensic evidence helps security teams identify and respond to malicious activity.
SaaS Alerts Indicators of Compromise (IoCs) allow users to create custom events within the application. Users can mix and match various occurrences to serve as indicators of compromise. This feature demonstrates to partners that they can generate their own IoCs whenever needed. The details can also include specific playbooks or actions that their technicians should implement.
Requirements
Please ensure you meet the following criteria:
-
You must have "MSP Admin" privileges in SaaS Alerts.
-
When using IoCs in conjunction with our Respond module, sign in using Microsoft, K1, or Google OAuth or Enable Multi-Factor Authentication (MFA) in the SaaS Alerts user settings.
-
Accept all security permissions required by the module.
NOTE If you choose to use Google, K1, or Microsoft Authentication, please remember to disable MFA.
Rules
-
Click Indicators of Compromise in the left pane.
-
On the Rules screen, partners can create new rules and manage existing ones.
Creating a rule
Before creating a rule, it's essential to understand its structure. Rules apply to one or more organizations and at least one account (typically a user account). Additionally, they must be "listening" for at least one event. Indicators of Compromise (IoCs) serve as "alerts only," which is similar to creating a new SaaS Alerts event.
To create a rule, follow these steps:
-
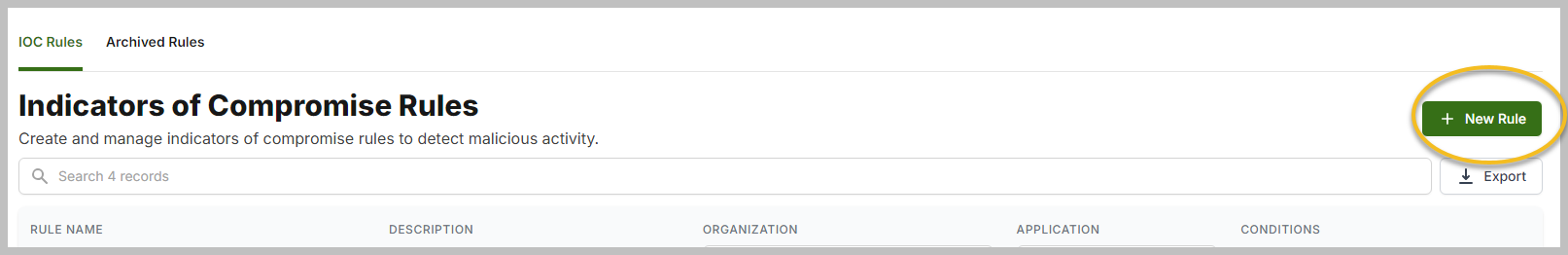
From the Indicators of Compromise screen, click + New Rule.
-
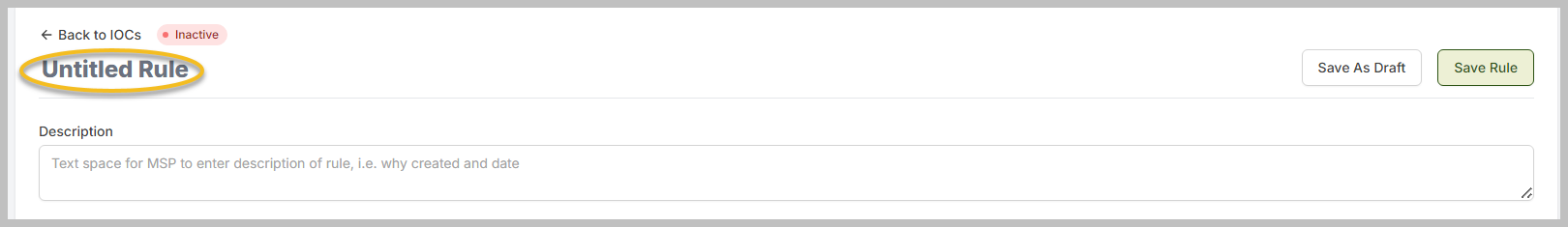
Click Untitled Rule to edit the name of the new rule.
-
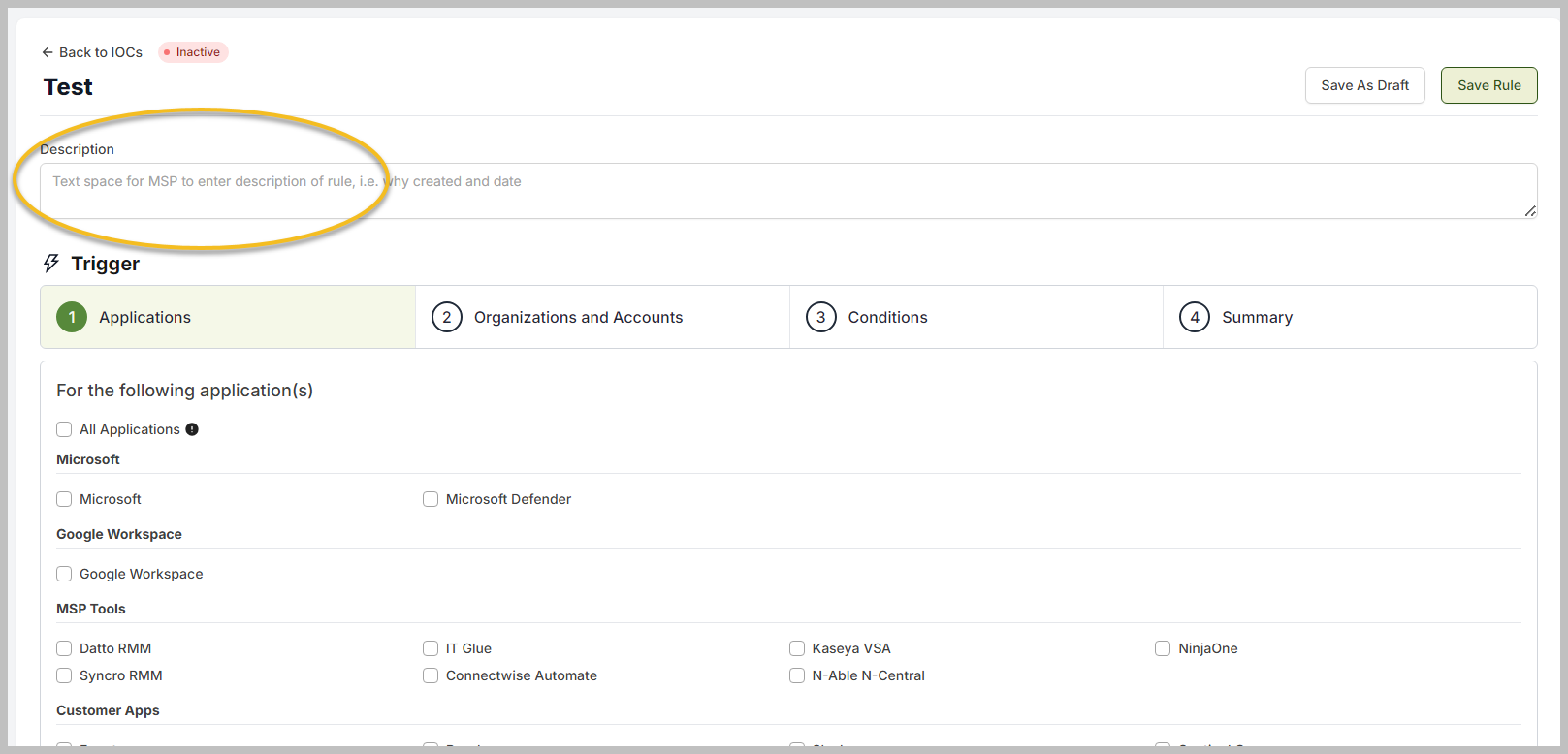
You can add a description to your IoC rule.
-
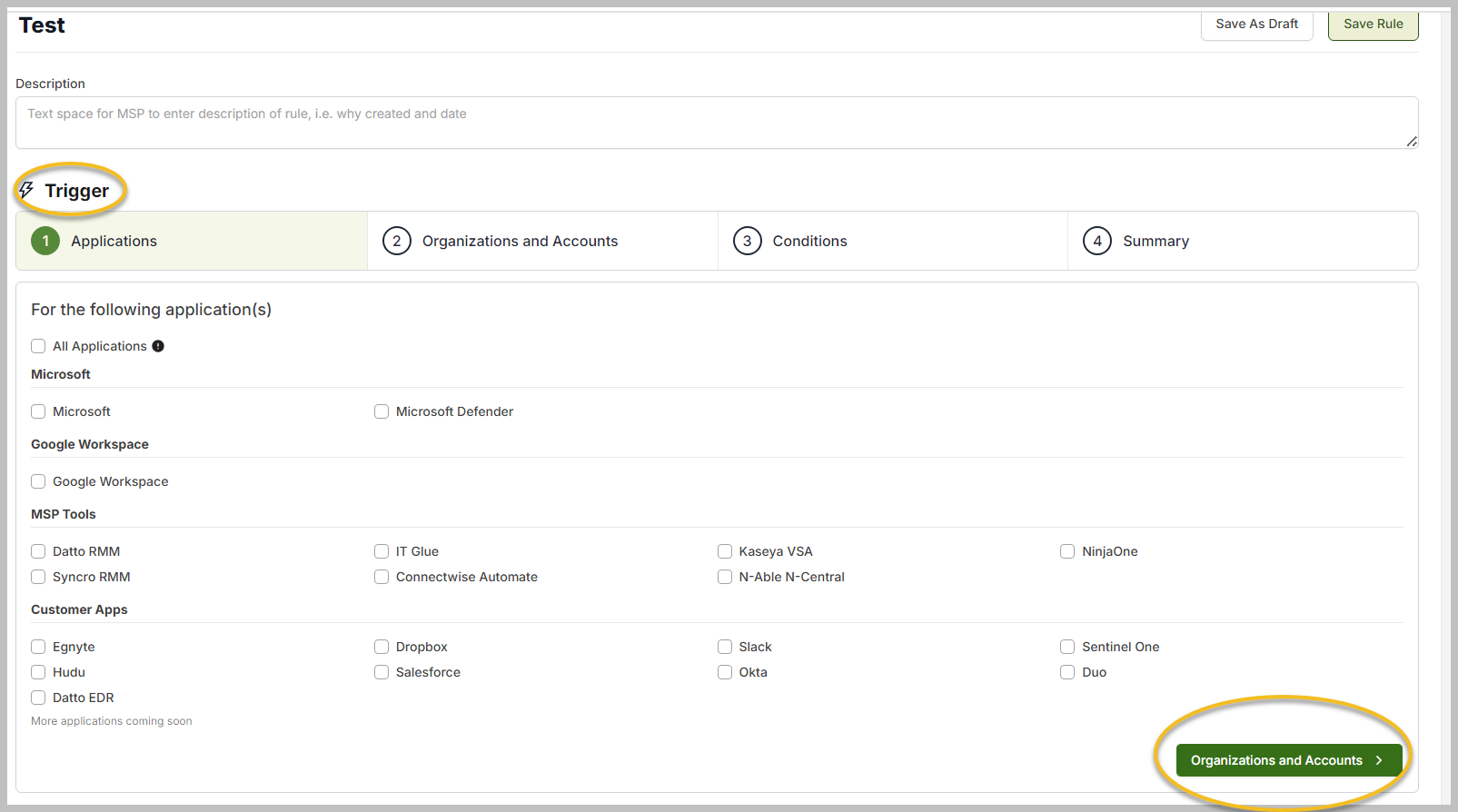
Under the Trigger section, select the application that you want to monitor. After that, click the Organizations and Accounts button.
-
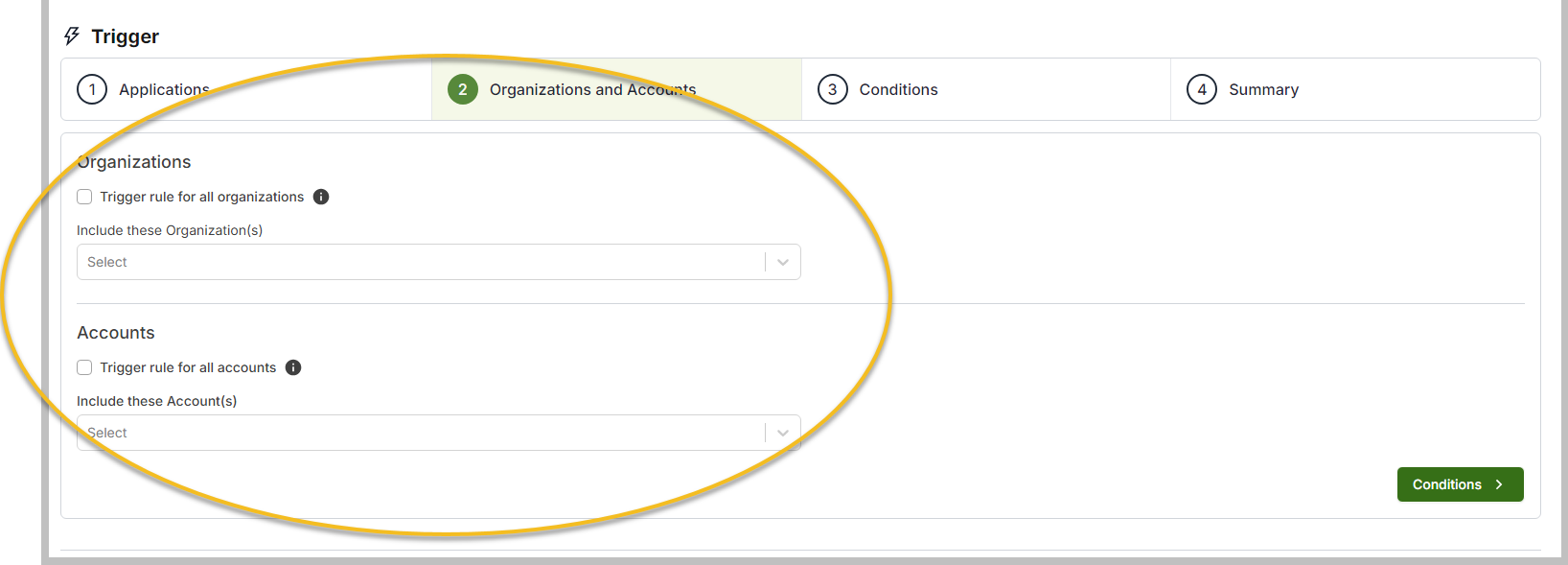
Select the organizations and accounts to be monitored. Partners can choose one, all, or multiple organizations and accounts.
NOTE If the option Trigger rules for all organizations or Trigger rules for all accounts is active, it will apply to all current and future organizations and accounts. By checking the Trigger rule for all organizations checkbox, you will also have the ability to exclude specific organizations.
-
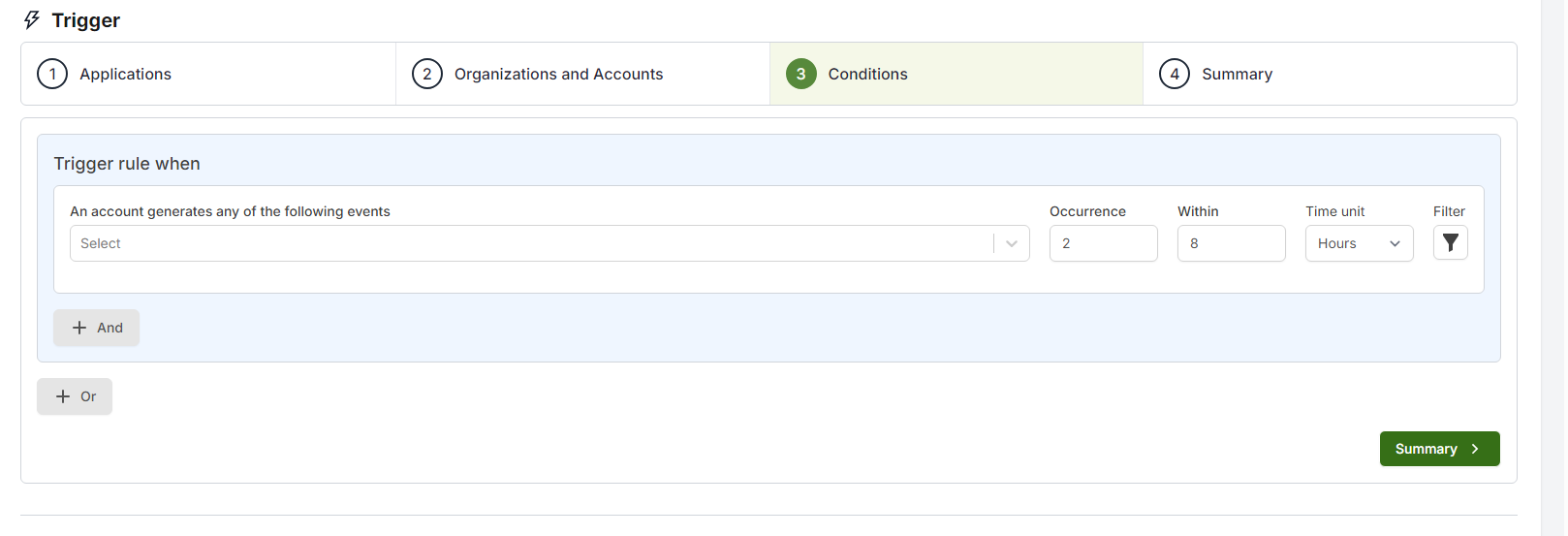
To proceed to the next screen, click the Conditions button.
Here, you can select the event or alert description that will trigger this rule. Choose the event, then specify the number of occurrences and the timeframe. The minimum number of occurrences is 1, and the minimum timeframe is 15 minutes. Additionally, partners have the option to add multiple events, either with the same or different parameters, and can combine them as needed. You can use logical OR and AND operators to create complex event monitoring flows.
NOTE IoCs will be scanned every five minutes to check for any conditions defined in the rule.
For each event selected in the rule, a filter can be applied. Filters enable the establishment of additional criteria based on specific event details. For example, you might use a filter such as Country contains US or Country does not contain US. This will determine whether instances of an event are included or excluded based on the specified filter.
-
Next, click the Summary button to review the Trigger section.
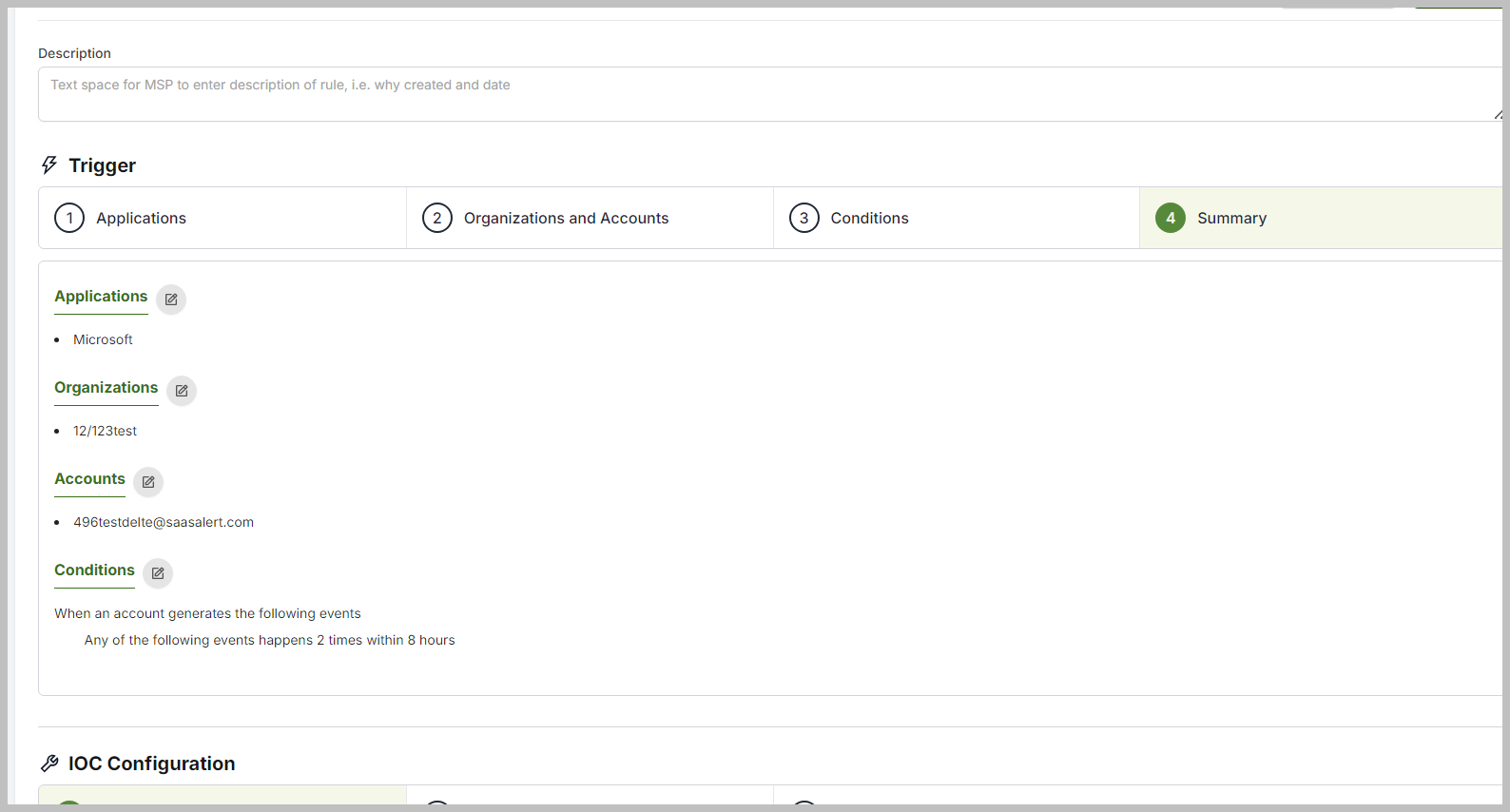
If you wish to add, change, or remove any of the Trigger settings, please click the edit pencil or the numbers to return to the previous screen. If everything appears to be correct, scroll down to proceed to the IOC Configuration section.
-
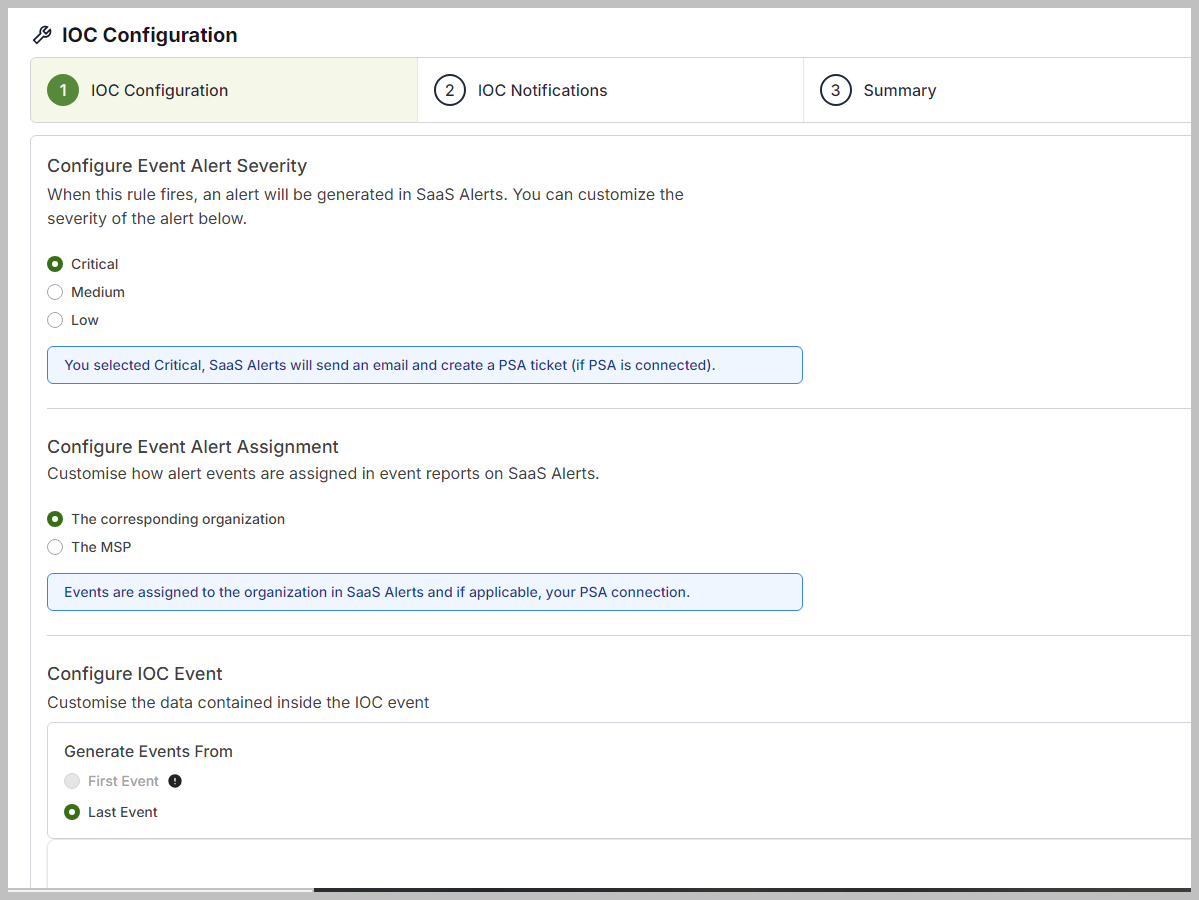
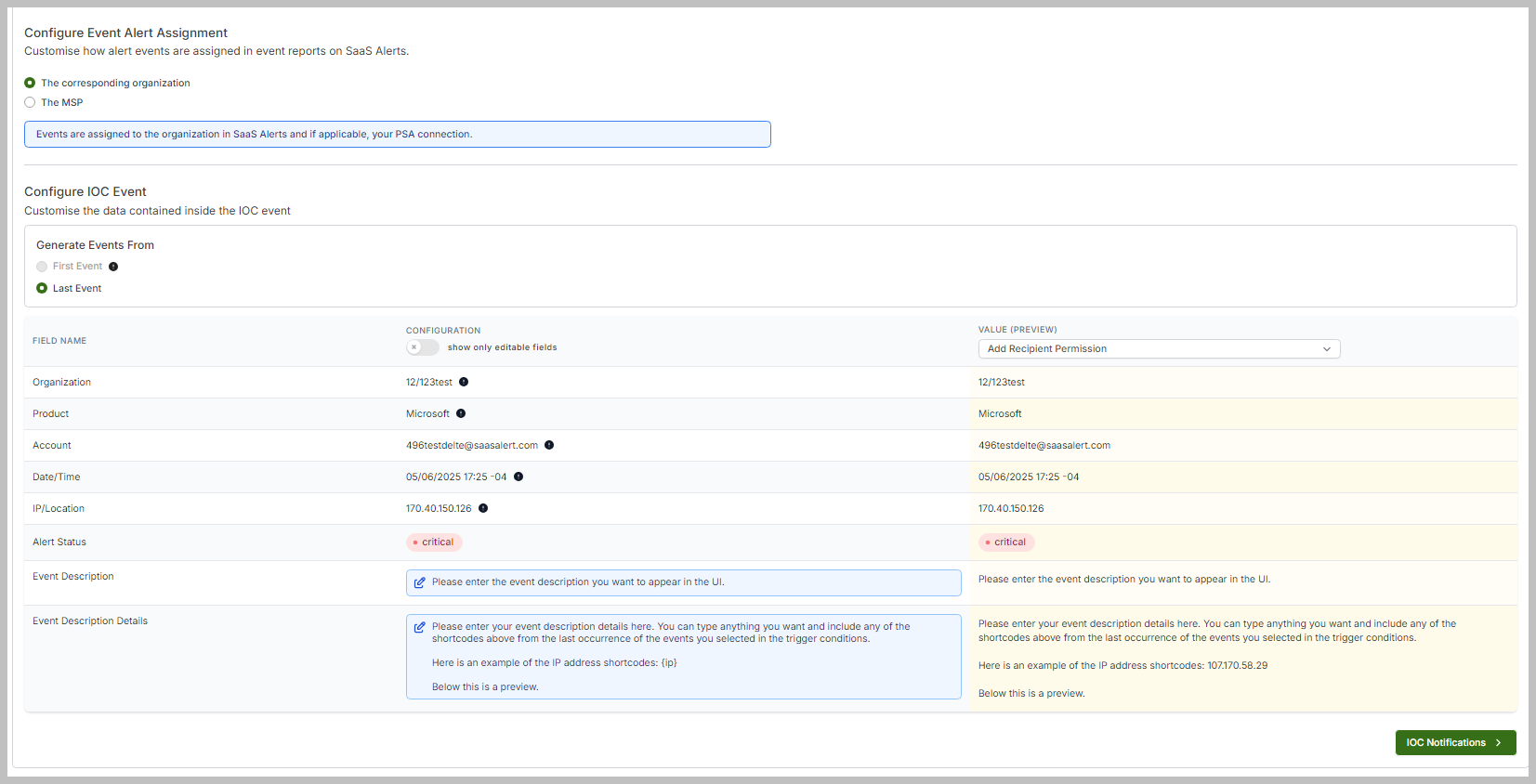
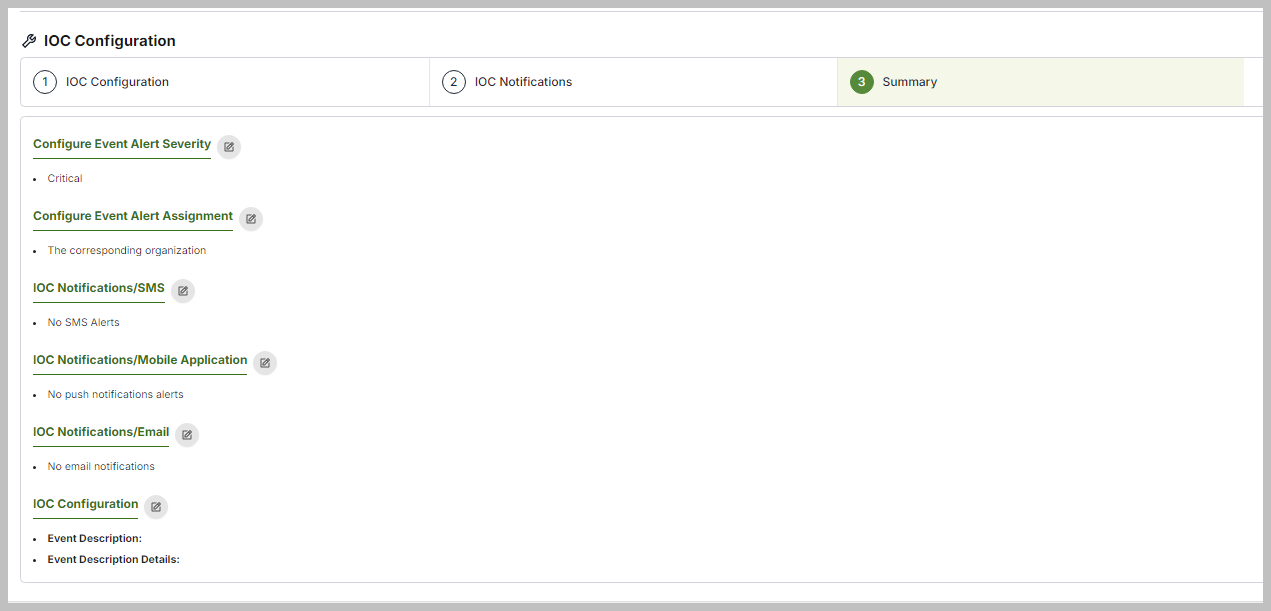
In the IOC Configuration section, partners have the option to customize the Alert Severity for created events, choosing between Critical, Medium, or Low. Additionally, you can configure the Event Alert Assignment, which allows you to tailor how events are assigned in Event Reports for SaaS Alerts.
-
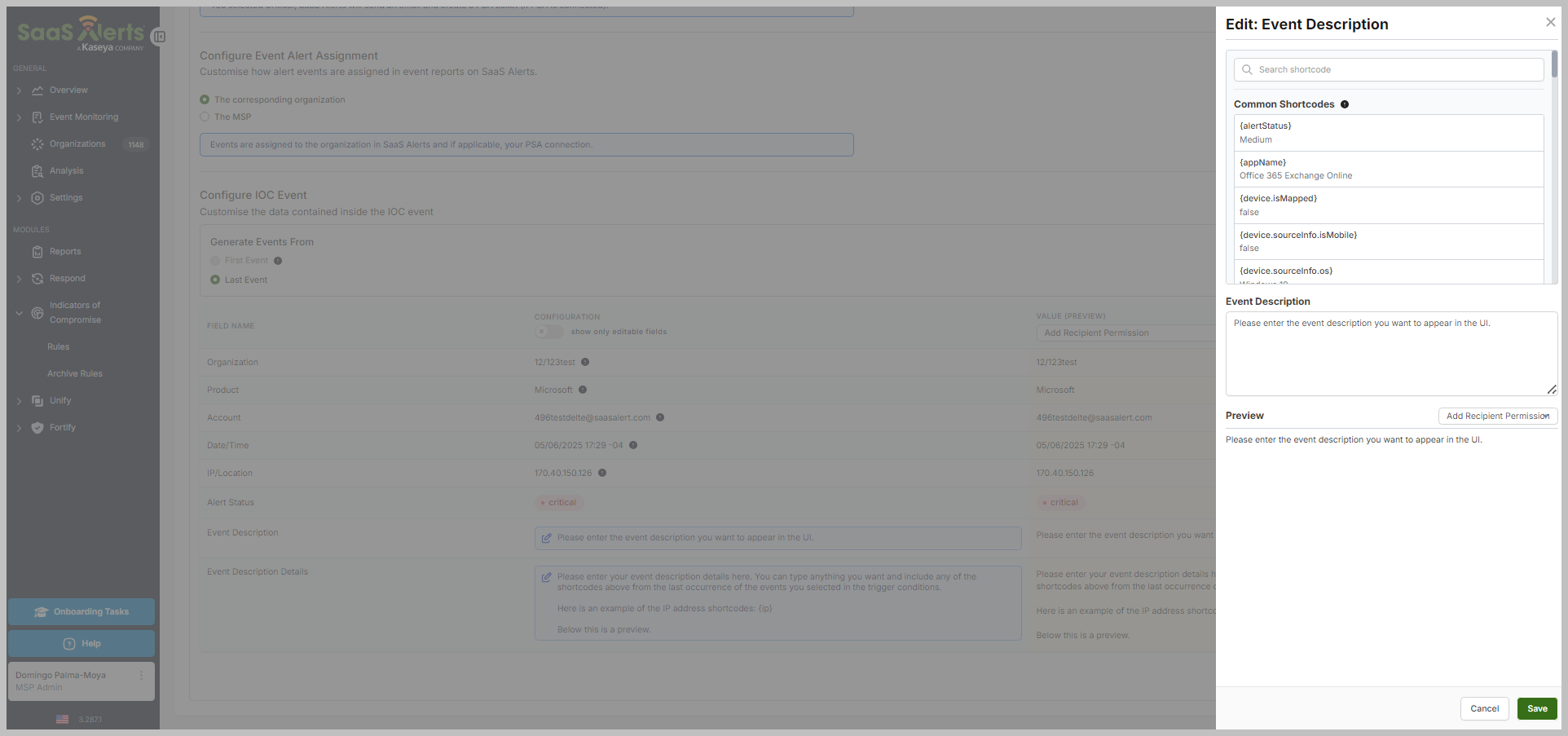
When configuring an IOC Event, you can customize the fields related to previously set events in the rule by clicking the blue boxes.
In the customization window, partners will see a selection of common short codes that they can choose from to include in their custom IoCs. Additionally, you have the option to assign a name to your new IoC alert or to write a description as needed.
-
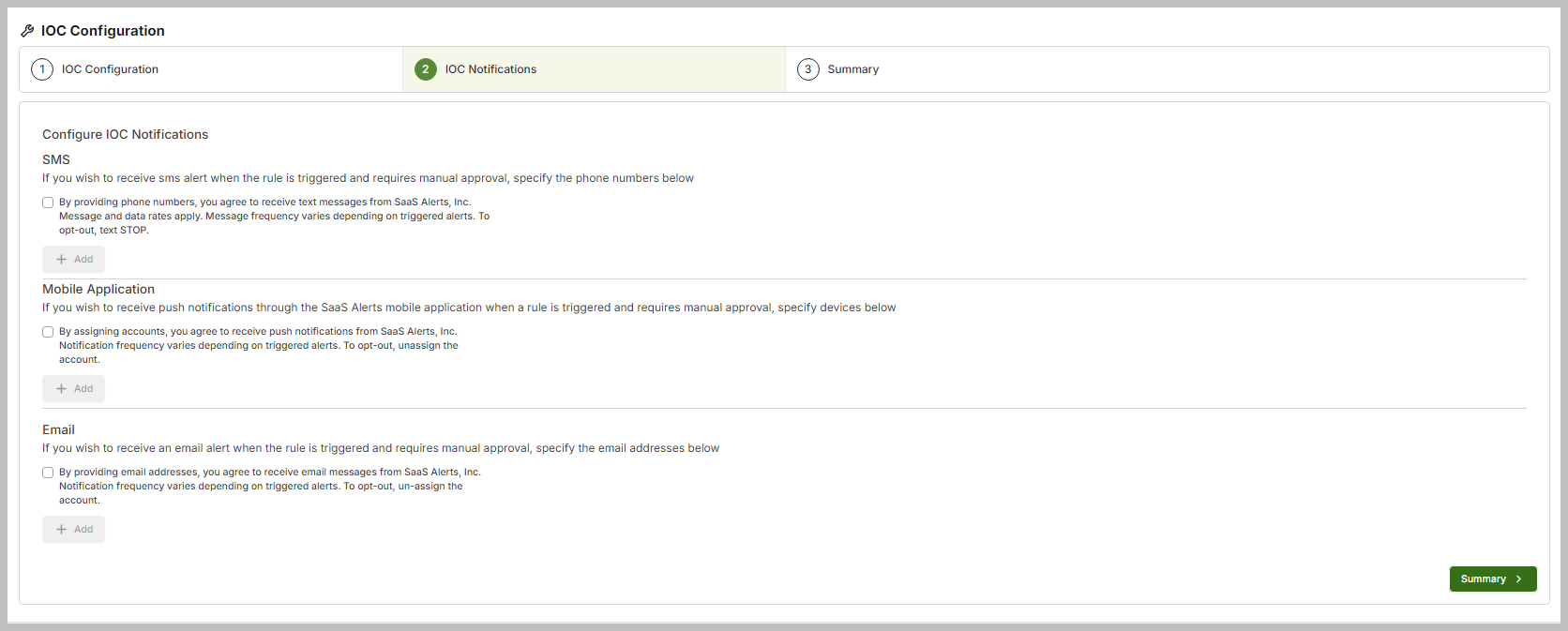
The IOC Notifications screen allows an MSP Admin to input a phone number, email address, or opt in for push notifications through the mobile app. This enables the admin to receive alerts when a rule is triggered. You can add multiple phone numbers and email addresses.
The initial step includes an explanation of the notifications you will receive, along with a checkbox that requires your approval to proceed.
-
Next, click the Summary button to review the IOC Configurations section.
If you wish to add, modify, or remove any of the IOC Configurations settings, please click the edit pencil icon or the numbers to return to the previous screen.
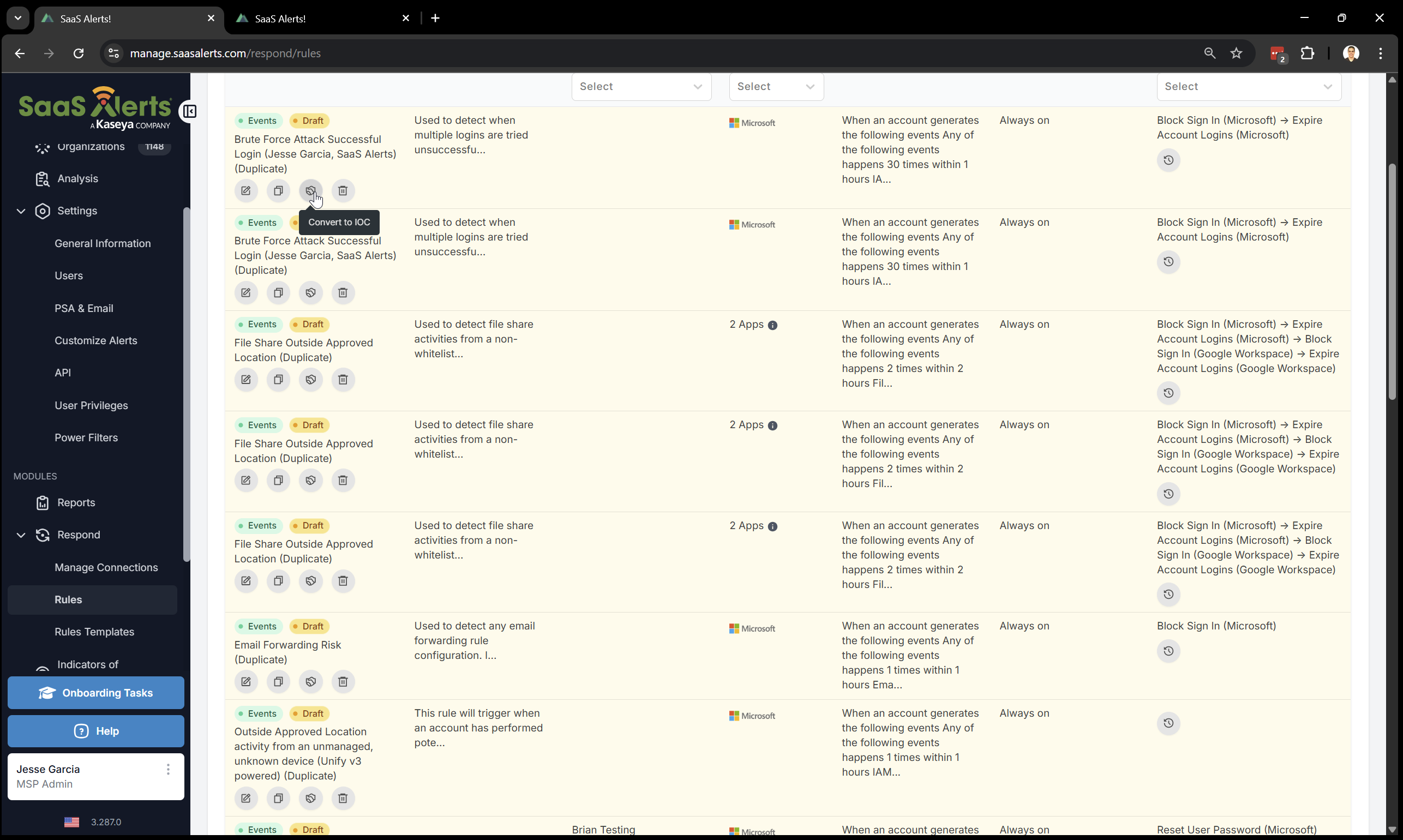
Respond Rules can be converted into an IoC by accessing the Respond rule and clicking the Convert to IOC button.